15 April 1998
Source:
http://www.fcw.com/pubs/fcw/1998/0413/web-nsareport-4-14-1998.html
Thanks to Federal Computer Week
See related FCW articles for NSA
comments:
http://www.fcw.com/pubs/fcw/1998/0406/fcw-polnsa-4-6-1998.html
http://www.fcw.com/pubs/fcw/1998/0413/web-nsacdt-4-14-1998.html
Note: This report was scanned in by FCW as a service to its readers. The charts appear as we received them. This is not an official NSA document.
This is a simple application of the SMI Threat and Vulnerability model to a generic system which provides key recovery (KR) to stored data and data in transit. The model includes a list of adversaries, their resources, and their motivations. It also includes a "vulnerability landscape," which describes the areas of attack. Finally, the model decomposes a key recovery system into its required functions, and the generic attacks against those functions. - This model could be used to assess a key recovery system as to how well it prevents the given adversaries from accomplishing their goals.
Adversary Model
The adversary model is made up of a list of potential adversaries, their typical capabilities in terms of monetary resources, access to the system, and tolerance for risk, and their objectives in attacking the key recovery system.
| Adversary | Risk Resources |
Access | Tolerance | Goals |
| Rogue User | Low | High | High | To circumvent the KR system |
| Various Espionage Adversaries | High | Low | High | To read the User's traffic |
| Rogue Key Recovery Personnel | Low | High | Low | Personal gain |
| Rogue Law Enforcement Agent | Medium | Medium | Medium | To gain unauthorized access users' traffic |
The rogue user is interested in circumventing the KR system so that his messages cannot be read by law enforcement (LE) or any other authority which has been granted that privilege by the KR system. In addition to law enforcement, other authorities could include the user's sponsoring organization or a national government. Note that if the sender and receiver both collaborate to defeat KR, there is no technical method from preventing this. So the design threshold for a KR system should take this fact into account.
The "various espionage adversaries" represent the typical threats to the user's privacy, which is the primary reason that the user needs to use encryption for his messages in the first place. The various espionage adversaries include organized crime, foreign intelligence, industrial espionage, hackers, and insiders. Their primary objective in attacking their targets KR system is to defeat the confidentiality mechanism and read their target's encrypted traffic.
The rogue key recovery personnel is that adversary who is trusted to keep confidential the users' KR secrets, that is, the insider threat at the Key Recovery Center. Although the rogue KR agent has an extremely high level of access, typically this adversary does not posses the resources or motivation necessary to collect the victim's traffic. The rogue KR agent may work on his own behalf, but is more likely to sell his high level of access to an adversary with more resources like organized crime or foreign intelligence. It is for this reason that KR agents must be highly trustworthy, and why the KR service should prudently be split between two independent KR agents.
The rogue law enforcement agent is representative of that set of adversaries who are granted authorized access by the KR system, but abuse this privilege. In addition to local law enforcement, this set of adversaries includes the users' organization, his local government, and in some cases, foreign governments. This adversary already has the necessary resources to conduct a wire tap against the victim, and will abuse his warranted access to steal the victim's KR secrets.
The primary goal of the espionage agents, rogue KR agents, and rogue LE agents is to read their targets' messages. If authentication is implied, either directly or indirectly, through the key recovery system, this set of adversaries might exploit the KR system to plant false evidence or forge messages. If the system depends on the proper invocation of the KR mechanism, this set of adversaries might use the KR system for a cheap denial of service attack. Keeping these possibilities in mind, the primary goal of these adversaries, for the rest of this report, is to read the users' encrypted traffic.
The Key Recovery Attack Tree
All attacks to the system are decomposed to fit into three categories: physical attacks, attacks against the life cycle of a product, and attacks against the trust model. Countermeasures which address these attacks can be subsequently applied to the attacks in each of these three categories. The attack tree is populated by iteratively deriving residual attacks in each category, and applying countermeasure to these attacks. This technique forces the analyst to study the threat and vulnerabilities of a given system in depth (down one category) as well as in breadth (across all categories).

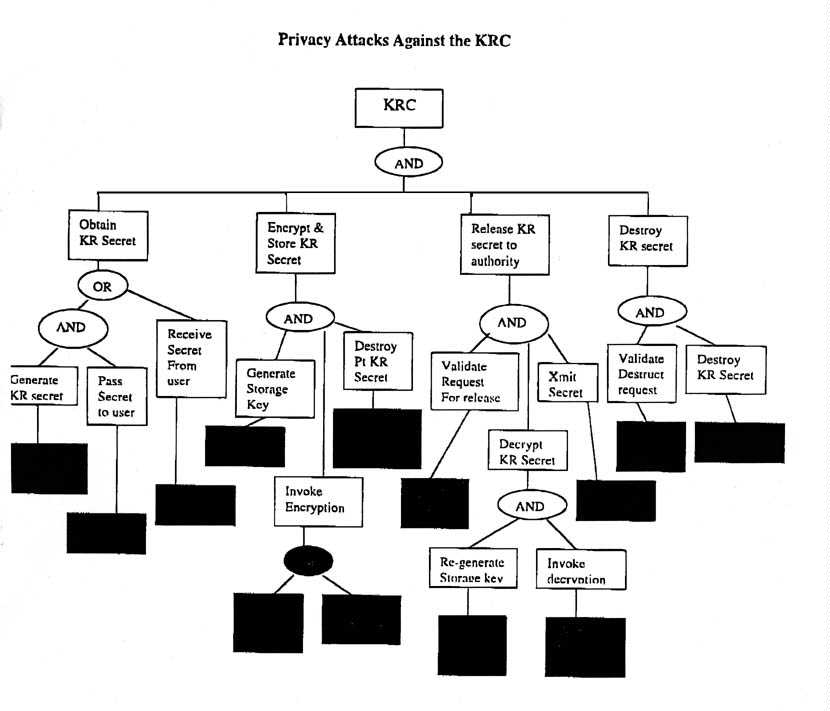
The Key Recovery Center makes an attractive target since a successful attack here has a huge return on investment.
A rogue Key Recovery agent, because of his high level of access, poses the most formidable threat, although may lack the motivation and risk tolerance to exploit this access. The rogue Law Enforcement Agent is also trusted with a high degree of access during the recovery process, and may be more motivated to exploit this access since he is already in the "wire tap" business. The espionage class of adversaries don't have any insider or warranted access to the, system, but they may have significantly more resources and determination than the other adversaries. If they cannot subvert the technical protection mechanisms at the Key Recovery Center, they may use their significant resources to buy off an insider, creating either a rogue law enforcement agent or rogue key recovery agent.
All of the attacks depicted in the attack tree above result in the compromise of a user's Key Recovery secret. The rogue user that wants to circumvent the Key Recovery mechanism will not conduct any privacy attacks, unless the user wants to publicly discredit the Key Recovery Center. Since the user's objective is to circumvent the KR mechanism, the attack tree associated with this objective looks different.
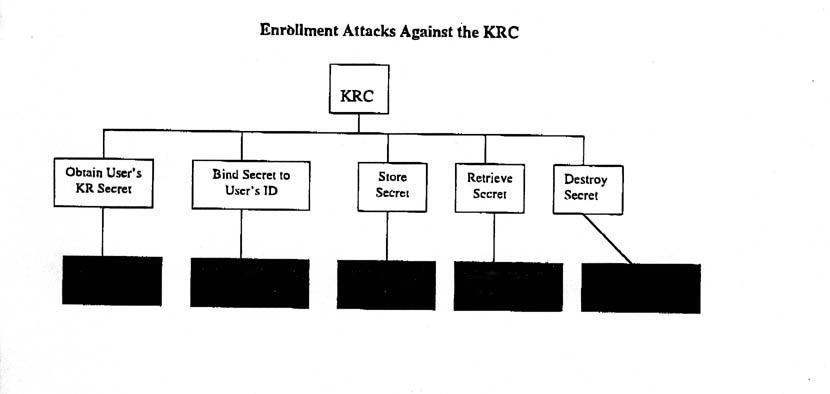
The enrollment process ac the KRC breaks down into five steps:
Encrypting a Message in Transit
The sender of a message performs three functions with respect to key recovery:
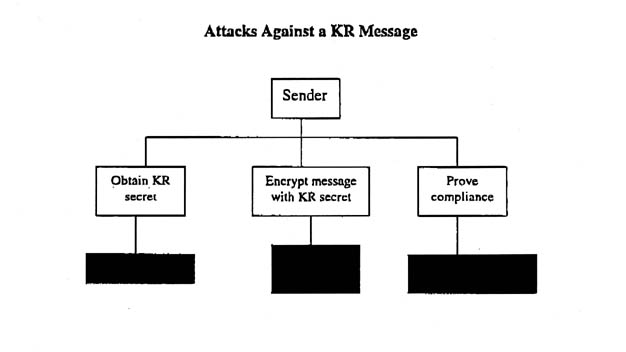
The receiver of the message needs only to verify that the sender complied with the KR mechanism, and takes the appropriate actions in accordance with the key recovery policy.
The sender of the message can circumvent the KR mechanism by fooling the receiver into believing that the message is key recovery enabled when, in fact, it is not. The receiver of the message typically cannot force the sender to circumvent the KR mechanism, however, in some cases, the receiver's compliance is necessary to recover the message, So, even the receiver of a message may be able to circumvent the KR mechanism.
A rogue KR or Law Enforcement agent who wants to read the encrypted message has no need to attack this part of the process, since they have much better access to the KR secret from the KR infrastructure. The various espionage agents may have better access to their targets than they do to the KRC, so this may be their best opportunity to attack.
Encrypting Store Data
The owner of a data performs three functions with respect to key recovery:
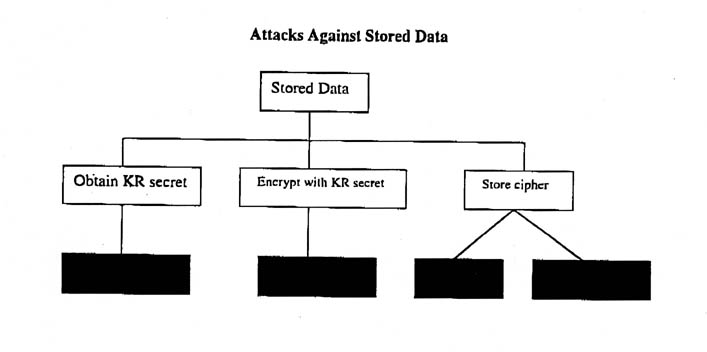
Encrypting stored data is the best opportunity for a rogue user to circumvent the KR mechanism and prevent Law Enforcement access, since enforcing compliance to the KR policy is impossible. Since access to the users' stored data may be harder to come by than access to data in transit, this may not be the best opportunity for the other adversaries to gather intelligence against their target.
Authorized Access
The Key Recovery system is designed to ultimately provide authorized access to encrypted messages. The process breaks down into three steps
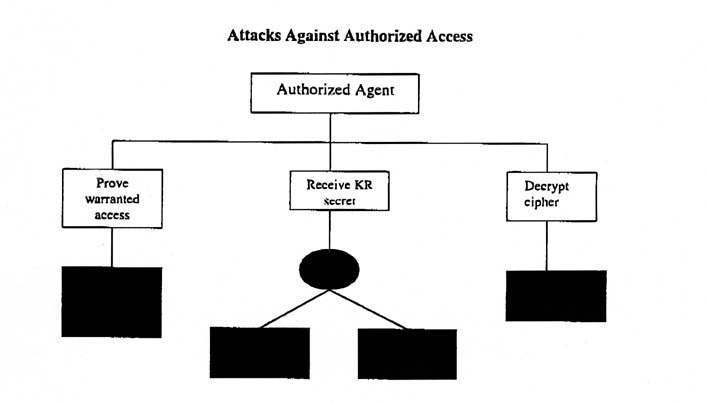
This authorized access service introduces new vulnerabilities for the set of adversaries. By simply abusing his privilege, spoofing the authorization function may be the best opportunity for a rogue law enforcement agent to attack the system and read a user's traffic. Depending on the protocols necessary before the KRC is allowed to give out the KR secret, stealing the KR secret during this process may be the best opportunity for the rogue KR agent. The various espionage agents may have the best access to the KR secret while it is being passed from the KRC to the authorized agent. The rogue user may be able to circumvent the KR mechanism by preventing the authorized agent from getting the correct KR secret, but this attack probably must be accomplished during the enrollment process while the KRC is interacting with the user.
Summary
1.2 During enrollment, the user will provide incorrect ID information to the KRC. This results in the KRC retrieving the wrong KR information when the KR service is invoked.
1.3 During an encrypted e-mail transmission. he rogue user does not invoke the KR mechanism properly, unbeknownst to the other participants
1.4 During encryption of a stored message, the rogue user does not invoke the KR mechanism properly,
In addition to circumventing the KR mechanism, the rogue user may want to discredit the KRC.
1.5 During enrollment or encryption, the rogue user provides incorrect ID information. This results in "key jacking", in which the law enforcement agent is able to read the encrypted message, but must de-escrow KR information that is not immediately associated with the target.
1.6 The rogue user will use his authorized access to the KRC to exploit the key recovery service and demonstrate its vulnerabilities
2. The Various Espionage Agents: The various espionage agents will attack the system at its weakest external point, since they do not have any special access or privilege.
2.2 The espionage agent will spoof the user into accepting and using KR information that is known to the espionage agent.
2.3 The espionage agent will steal the secret KR information from the KRC. This results in the loss of all users' KR information, making the KRC a lucrative target for this class of adversary.
2.4 During authorized release of the KR information, the espionage agent will exploit the transmission of secret information as it is passed between the KRC and the authorized recipient.
2.5 The espionage agent will spoof the KRC into releasing secret KR information by masquerading as someone with authorized access.
III Rogue KR Personnel: The rogue KR agent has access to the KR secret at all times during its life cycle. The rogue KR agent simply waits for the proper motivation to exploit his victims.
3.2 At any time during the storage of the KR information, the rogue KR agent invokes the KR service to extract the KR information in a useful form.
3.3 During a legitimate, authorized access, the rogue KR agent saves a copy of the secret KR information.
If the KR agent has a personal interest in the target of a legal wiretap as in a corporate key recovery service, the rogue KR agent may want to subvert the law enforcement access.
3.4 The rogue KR agent win fail to provide the key recovery service in an accurate or timely manner.
3.5 The rogue KR agent will notify the target of the investigation of the pending wiretap.
4. Rogue Law Enforcement Agent: The rogue LE agent's best opportunity to gain unwarranted access to his target's information is simply to just ask for it.
4.2 The rogue LE agent will spoof the KRC into believing that warranted access has been granted, when, in fact, it has not been granted.